Why I stay away from Windows? --One of the main reasons is security, or the lack of it. Windows operating system is simply far more vulnerable to viruses and worms compared to Linux or Mac OS X. I don’t want to explain further or start a debate here, but I’ll just let this all time list of 12 most devastating viruses and worms do the talking.
1. ILOVEYOU VIRUS
The ILOVEYOU worm (a.k.a. VBS/Loveletter and Love Bug worm), a computer worm written in VBScript, is considered by many as the most damaging worm ever. It started in the Philippines on May 4, 2000, and spread across the world in one day (traveling from Hong-Kong to Europe to the United States), infecting 10 percent of all computers connected to the Internet and causing about $5.5 billion in damage. Most of the "damage" was the labor of getting rid of the virus. The worm arrived in e-mail boxes with the simple subject of "ILOVEYOU" and an attachment "LOVE-LETTER-FOR-YOU.TXT.vbs". The Pentagon, CIA, and the British Parliament had to shut down their e-mail systems to get rid of the worm, as did most large corporations.
The worm overwrote important files, as well as music, multimedia and more, with a copy of itself. It also sent the worm to everyone on a user's contact list. This particular worm only affected computers running the Microsoft Windows operating system. While any computer accessing e-mail could receive an "ILOVEYOU" e-mail, only Microsoft Windows systems would be infected. The worm propagates by sending out copies of itself to all entries in the Microsoft Outlook address book. It also has an additional component, in which it will download and execute an infected program called variously "WIN-BUGSFIX.EXE" or "Microsoftv25.exe". This is a password-stealing program which will e-mail cached passwords.
The ILOVEYOU worm is believed to have been written by Burningice & Moon. The Barok trojan horse used by the worm is believed to have been written by dark_tech, a Filipino student of AMA Computer University in Makati, Philippines.
Right now you never can tell if the ILOVE Worm is currently running in your PC. If you notice your PC is beginning to run very slow then theres definitely a strong malware at work. Many antivirus softwares have proven uncessful while trying to fetch out this deadly ILOVEYOU virus but thanks to YAC Malware remover which has been proven to be the best in combating the ILOVEYOU virus and also speeding up your computer after moping out every single traces of the ILOVEYOU virus from your device.
Download YAC Malware remover


2. Mydoom
Mydoom, also known as W32.MyDoom@mm, Novarg, Mimail.R and Shimgapi, is a computer virus affecting Microsoft Windows. It was first sighted on January 26, 2004 and became the fastest-spreading e-mail worm ever, exceeding previous records set by the Sobig worm.
Mydoom is primarily transmitted via e-mail, appearing as a transmission error, with subject lines including “Error”, “Mail Delivery System”, “Test” or “Mail Transaction Failed” in different languages, including English and French. The mail contains an attachment that, if executed, resends the worm to e-mail addresses found in local files such as a user's address book. It also copies itself to the “shared folder” of peer-to-peer file-sharing application KaZaA in an attempt to spread that way.
Mydoom appears to have been commissioned by e-mail spammers so as to send junk e-mail through infected computers. The worm contains the text message “andy; I'm just doing my job, nothing personal, sorry,” leading many to believe that the worm's creator was paid to do so. Early on, several security firms published their belief that the worm originated from a professional underground programmer in Russia. The actual author of the worm is unknown.
4. Sobig Worm
The Sobig Worm was a computer worm that infected millions of Internet-connected, Microsoft Windows computers in August 2003. It was written using the Microsoft Visual C++ compiler, and subsequently compressed using a data compression program called tElock. There are plenty of variants of the Sobig worm, but the most destructive and widespread of all is called Sobig.F.
Sobig is a computer worm in the sense that it replicates by itself, but also a Trojan horse in that it masquerades as something other than malware. The Sobig worm will appear as an electronic mail and will contain the text: "See the attached file for details" or "Please see the attached file for details."
.The Sobig.F worm deactivated itself on September 10, 2003. On November 5 the same year, Microsoft announced that they will pay $250,000 for information leading to the arrest of the creator of the Sobig worm. To date, the perpetrator has not been caught.
5. Code Red
The Code Red worm was a computer worm observed on the Internet on July 13, 2001. It attacked computers running Microsoft's IIS web server. The most in-depth research on the worm was performed by the programmers at eEye Digital Security. They also gave the worm the phrase "Hacked By Chinese!" with which the worm defaced websites. Although the worm had been released on July 13, the largest group of infected computers was seen on July 19, 2001. On this day, the number of infected hosts reached 359,000.
Effects of Code Red:
* It defaced the affected web site to display:
HELLO! Welcome to http://www.worm.com! Hacked By Chinese!
(The last sentence became a cliché to indicate an online defeat)
* It tried to spread itself by looking for more IIS servers on the Internet.
* It waited 20-27 days after it was installed to launch denial of service attacks on several fixed IP addresses. The IP address of the White House web server was among those.
eEye believed that the worm originated in Makati City, Philippines (the same origin as the VBS/Loveletter (aka "ILOVEYOU") worm)
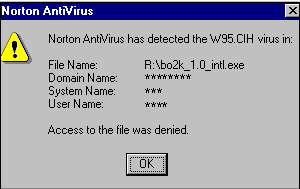
6. CIH
CIH, also known as Chernobyl or Spacefiller, is a computer virus written by Chen Ing Hau of Taiwan. It is considered to be one of the most harmful widely circulated viruses, overwriting critical information on infected system drives, and more importantly, in some cases corrupting the system BIOS.
The name "Chernobyl Virus" was coined some time after the virus was already well-known as CIH, and refers to the complete coincidence of the payload trigger date in some variants of the virus (actually the virus writer's birthday) and the Chernobyl accident, which happened in Ukraine on April 26, 1986. Today, CIH is not as widespread as it once was, due to awareness of the threat and the fact it only affects older Windows 9x (95, 98, Me) operating systems.
The virus made another comeback in 2001 when a variant of the Loveletter Worm in a VBS file that contained a dropper routine for the CIH virus was circulated around the internet, under the guise of a nude picture of Jennifer Lopez.
7. Klez
Klez is a computer worm that propagates via e-mail. It first appeared in the end of 2001. A number of variants of the worm exist. Klez infects Microsoft Windows systems, exploiting vulnerability in Internet Explorer's Trident layout engine, used by both Microsoft Outlook and Outlook Express to render HTML mail.
The e-mail through which the worm spreads always includes a text portion and one or more attachments. The text portion consists of either an HTML internal frame tag which causes buggy e-mail clients to automatically execute the worm, or a few lines of text that attempt to induce the recipient to execute the worm by opening the attachment (sometimes by claiming that the attachment is a patch from Microsoft; sometimes by claiming that the attachment is an antidote for the Klez worm). The first attachment is always the worm, whose internals vary.
Later variants of the worm would use a false “From” address, picking an e-mail address at random from the infected machine's Outlook or Outlook Express address book, making it impossible for casual observers to determine which machine is infected, and making it difficult for experts to determine anything more than the infected machine's Internet Service Provider.
8. Melissa
The Melissa worm, also known as "Mailissa", "Simpsons", "Kwyjibo", or "Kwejeebo", is a mass-mailing macro virus, hence leading some to classify it as a computer worm. First found on March 26, 1999, Melissa shut down Internet mail systems that got clogged with infected e-mails propagating from the worm. Melissa was not originally designed for harm, but it overflowed servers and caused unplanned problems.
Melissa can spread on word processors Microsoft Word 97 and Word 2000. It can mass-mail itself from e-mail client Microsoft Outlook 97 or Outlook 98. The worm does not work on any other versions of Word, including Word 95, Microsoft Office Word 2003, Word 2004 (Mac), and Microsoft Office Word 2007, nor can it mass-mail itself via any other e-mail client, even Outlook Express or Windows Mail (Outlook Express version in Windows Vista).
Melissa was first distributed in the Usenet discussion group alt.sex. The virus was inside a file called "List.DOC", which contained passwords that allow access into 80 pornographic websites. The worm's original form was sent via e-mail to many people.
9. Sasser
Sasser (sometimes known as the Big One) is a computer worm that affects computers running vulnerable versions of the Microsoft operating systems Windows XP and Windows 2000. Some machines running Windows 98 were infected. Like other worms, Sasser spreads by exploiting the system through a vulnerable network port. Thus it is particularly potent in that it can spread without user intervention, but it is also easily stopped by a properly configured firewall or by downloading system updates from Windows Update. Sasser was first noticed and started spreading on April 30, 2004. This worm was named Sasser because it spreads by exploiting a buffer overflow in the component known as LSASS (Local Security Authority Subsystem Service) on the affected operating systems.
The effects of Sasser include the news agency Agence France-Presse (AFP) having all its satellite communications blocked for hours and the U.S. flight company Delta Air Lines having to cancel several trans-atlantic flights because its computer systems had been swamped by the worm. The Nordic insurance company If and their Finnish owners Sampo Bank came to a complete halt and had to close their 130 offices in Finland. The British Coastguard had its electronic mapping service disabled for a few hours, and Goldman Sachs, Deutsche Post, and the European Commission also all had issues with the worm. The X-ray department at Lund University Hospital had all their four layer X-ray machines disabled for several hours and had to redirect emergency X-ray patients to a nearby hospital.
Sasser was at first believed to have been authored in Russia by the same person(s) who created another worm usually referred to as Lovsan, MSBlast or Blaster (due to the media), a connection indicated by code similarities between the two, but on May 7, 2004, 18-year old German computer science student Sven Jaschan from Rotenburg, Lower Saxony was arrested for writing the worm.
10. Bagle
Bagle (also known as Beagle) is a mass-mailing computer worm written in pure assembly and affecting all versions of Microsoft Windows. The first strain, Bagle.A, did not propagate widely. A second variation, Bagle.B is considerably more virulent. Bagle uses its own SMTP engine to mass-mail itself as an attachment to recipients gathered from the victim computer.
The second strain, Bagle.B, was first sighted on February 17, 2004. It was much more widespread and appeared in large quantities; Network Associates rated it a "medium" threat. It is designed to stop spreading after February 25, 2004.
Subsequent variants have later been discovered. Although they have not all been successful, a number remain notable threats. Since 2004, the threat risk from these variants has been changed to "low" due to decreased prevalence.
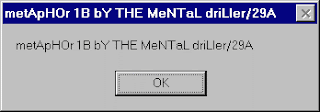
11. Win32/Simile
Win32/Simile (also known as Etap) is a metamorphic computer virus written in assembly language for Microsoft Windows. The virus was released in the most recent version in early March 2002. It was written by the virus writer Mental Driller. Some of his previous viruses, such as Win95/Drill (which used the Tuareg polymorphic engine), have proved very challenging to detect.
When the virus is first executed, it checks the current date. If the host file (the file that is infected with the virus) imports the file User32.dll, then on the 17th of March, June, September, or December, a message is displayed. Depending on the version of the virus the case of each letter in the text is altered randomly. On May 14 (the anniversary of Israeli Independence Day), a message saying "Free Palestine!" will be displayed if the system locale is set to Hebrew.
The virus then rebuilds itself. This metamorphic process is very complex and accounts for around 90% of the virus' code. After the rebuild, the virus searches for executable files in folders on all fixed and remote drives. Files will not be infected if they are located in a subfolder more than three levels deep, or if the folder name begins with the letter W. For each file that is found, there is a 50 percent chance that it will be ignored. Files will not be infected if they begin with F, PA, SC, DR, NO, or if the letter V appears anywhere in the file name. Due to the way in which the name matching is done, file names that contain certain other characters are also not infected, although this part is not deliberate. The virus contains checks to avoid infecting "goat" or "bait" files (files that are created by anti-virus programs). The infection process uses the structure of the host, as well as random factors, to control the placement of the virus body and the decryptor.
12. Nimda
Nimda is a computer worm, isolated in September 2001. It is also a file infector. It quickly spread, eclipsing the economic damage caused by past outbreaks such as Code Red. Multiple propagation vectors allowed Nimda to become the Internet’s most widespread virus/worm within 22 minutes. Due to the release date, some media quickly began speculating a link between the virus and Al Qaeda, though this relationship ended up being untrue. Nimda affected both user workstations (clients) running Windows 95, 98, Me, NT, or 2000 and servers running Windows NT and 2000. The worm's name spelled backwards is "admin".
Nimda was so effective partially because it—unlike other famous malware like the Morris worm or Code Red—uses five different infection vectors:
-via email
- via open network shares
- via browsing of compromised web sites
- exploitation of various Microsoft IIS 4.0 / 5.0 directory traversal vulnerabilities. (Both Code Red, and Nimda were hugely successful exploiting well known and long solved vulnerabilities in the Microsoft IIS server.)
- via back doors left behind by the "Code Red II" and "sadmind/IIS" worms.
The author of Nimda is suspected to be a former student who attended Sacramento State University Fall of 2001.
Share this page with others. You never can tell who would be saved just by receiving a share of this post
Click on the buttons below to share.